Security researchers find critical flaws in mainstream password managers
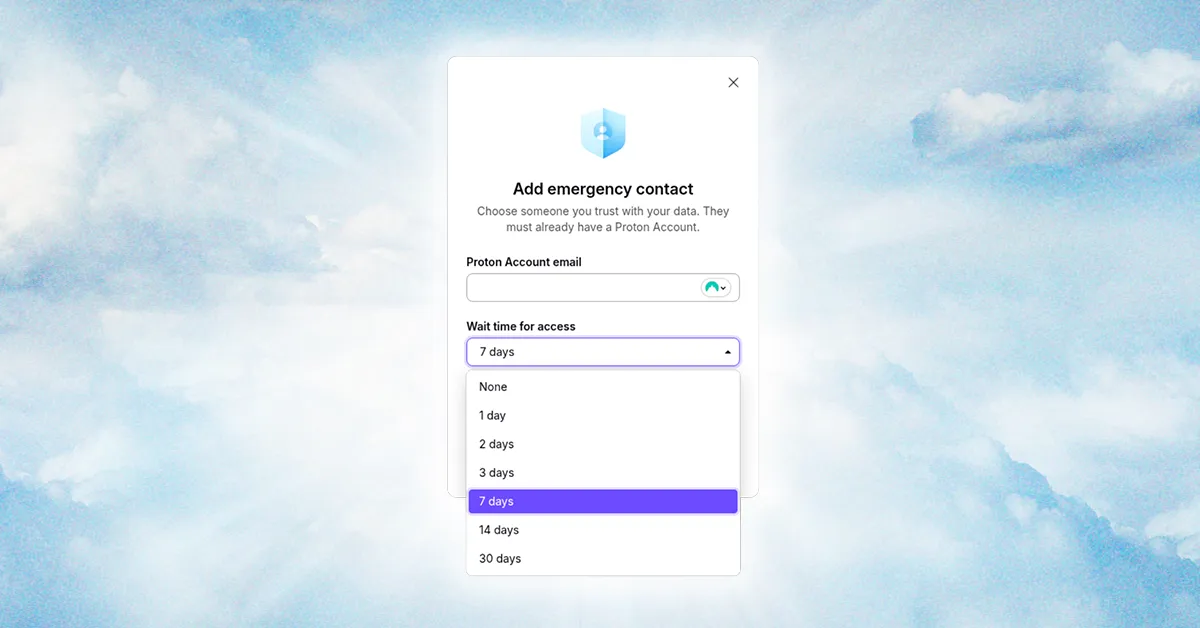
An ETH Zurich team tested Bitwarden, LastPass, and Dashlane under a malicious-server threat model and demonstrated 12, 7, and 6 attacks respectively, showing that passwords could be accessed or altered and that end-to-end, zero-knowledge encryption promises may not hold. They found the attacks often only required routine user actions like logging in or syncing. The researchers propose updating cryptographic standards for new customers, providing migration paths for existing users, and increasing transparency via external audits, noting that many providers still rely on outdated crypto. Consumers should favor password managers that disclose vulnerabilities, are audited, and enable end-to-end encryption by default.