X Users: Re-Enroll Security Keys and Update Accounts Before November 10 to Prevent Lockouts
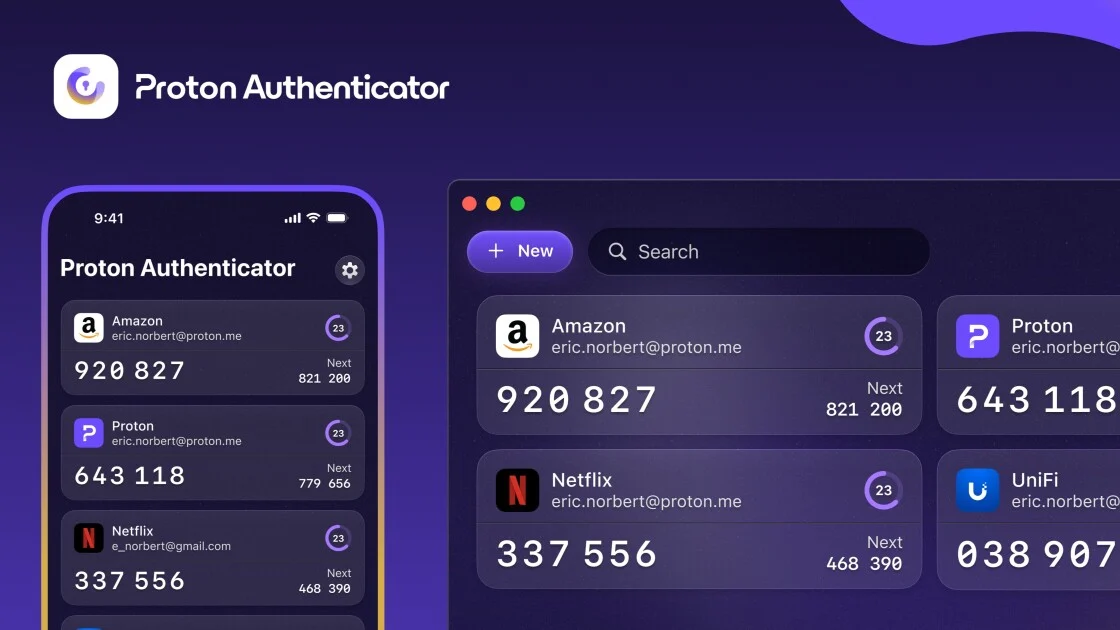
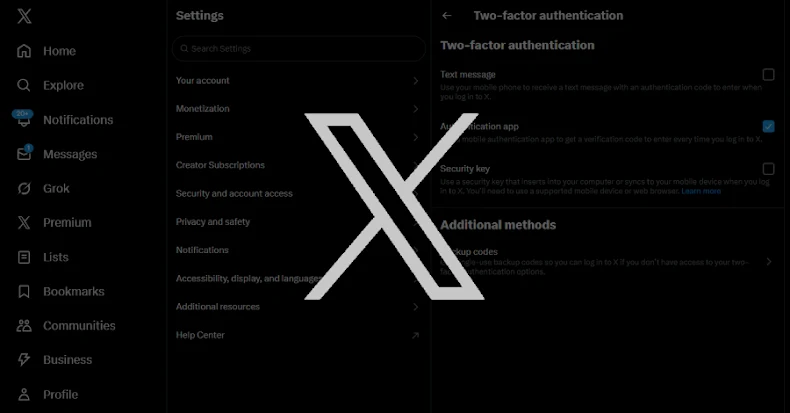
X is urging users with security keys for two-factor authentication to re-enroll their keys by November 10, 2025, to avoid account lockouts and to facilitate the transition from the twitter.com domain to x.com, with re-enrollment required only for security key users, not those using other 2FA methods.