MongoDB Vulnerabilities: Critical Flaws and Urgent Patching Alerts
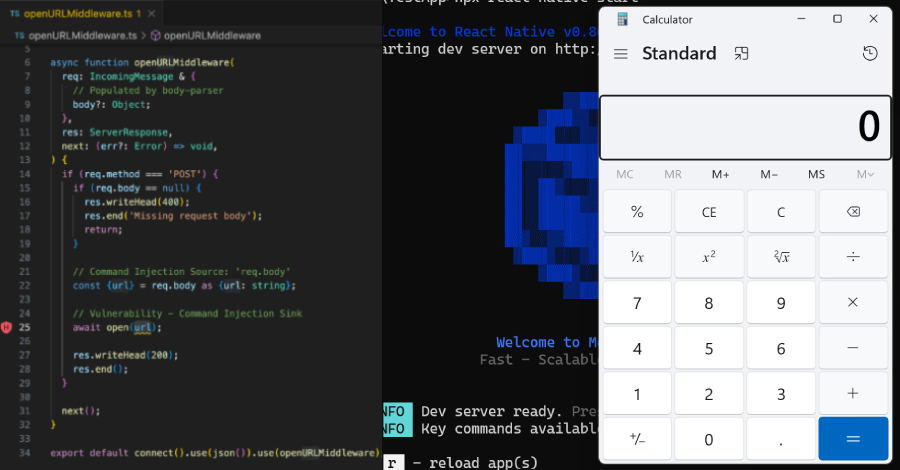
A critical security vulnerability in MongoDB (CVE-2025-14847) allows unauthenticated attackers to read uninitialized heap memory, potentially exposing sensitive data. The flaw affects multiple versions and has been patched in newer releases; users are advised to upgrade or disable zlib compression to mitigate risks.