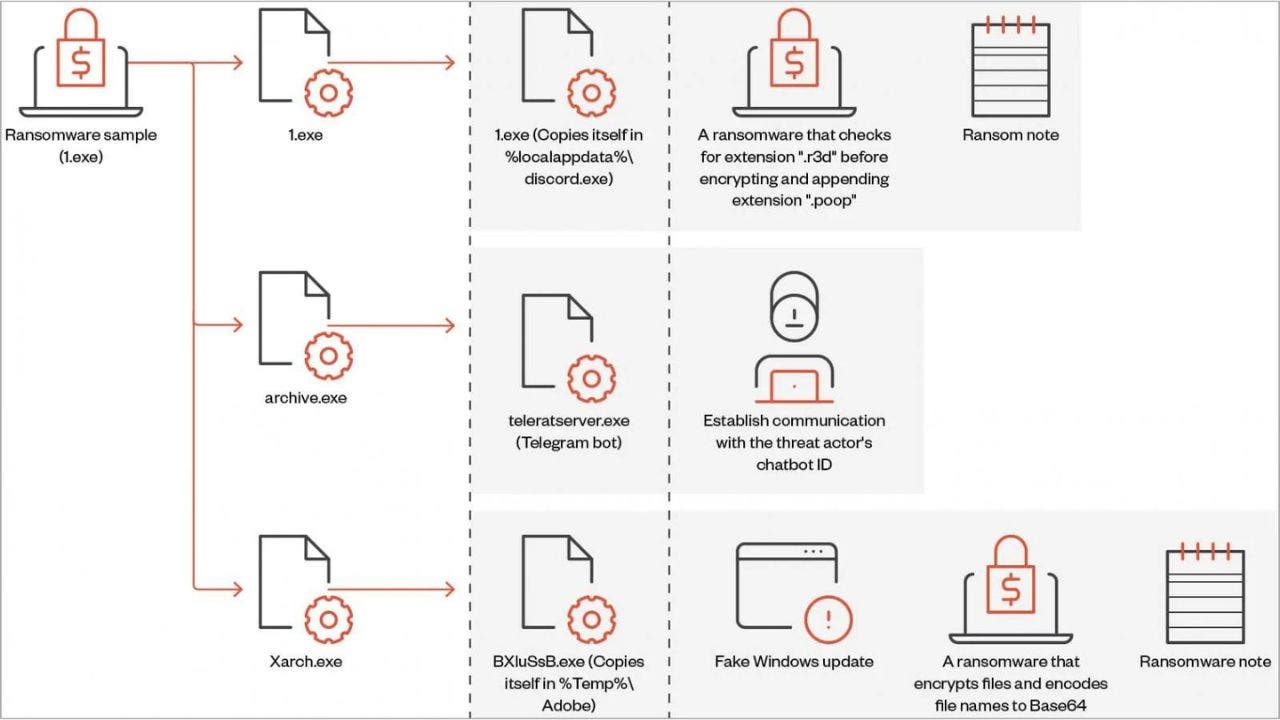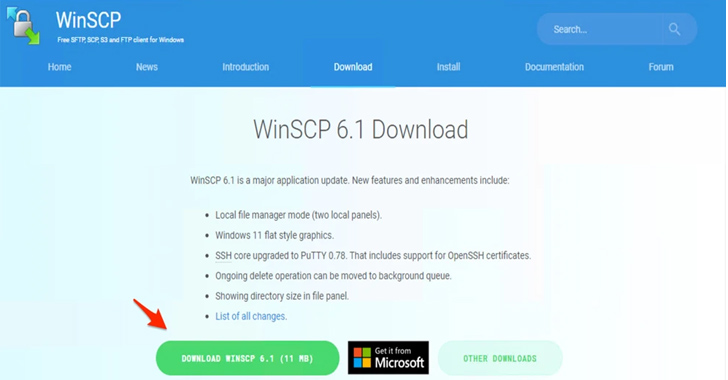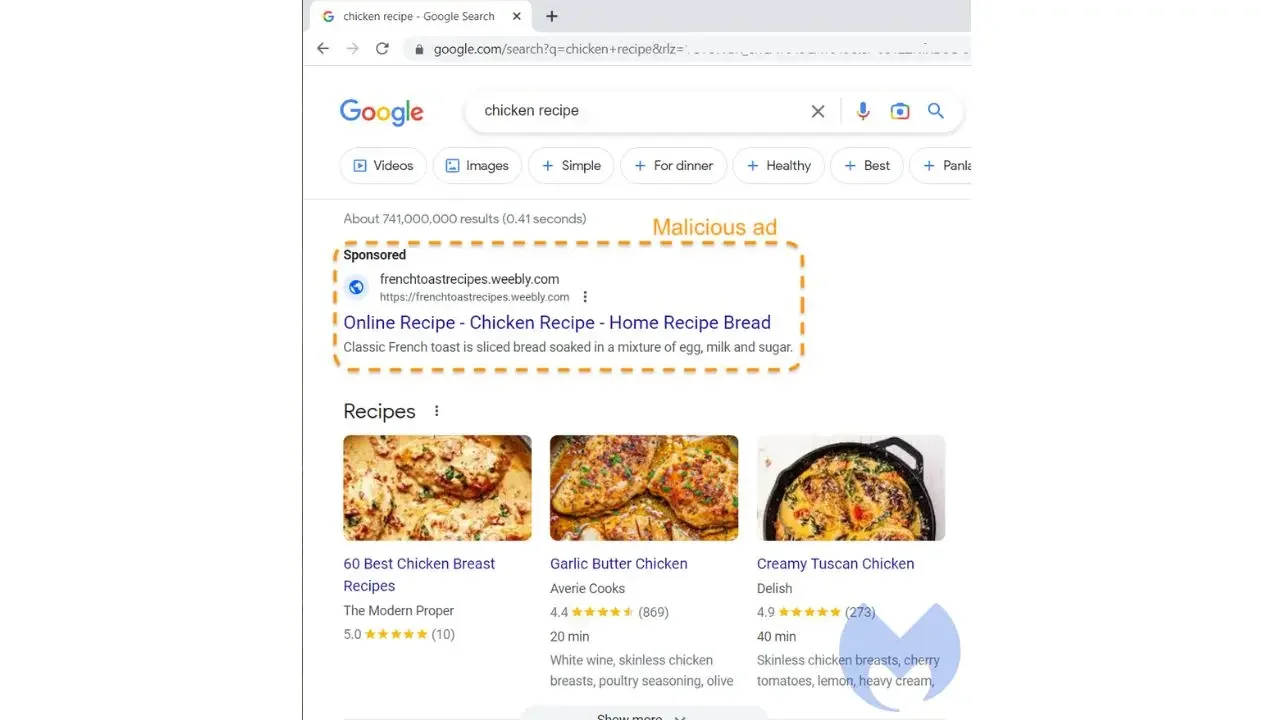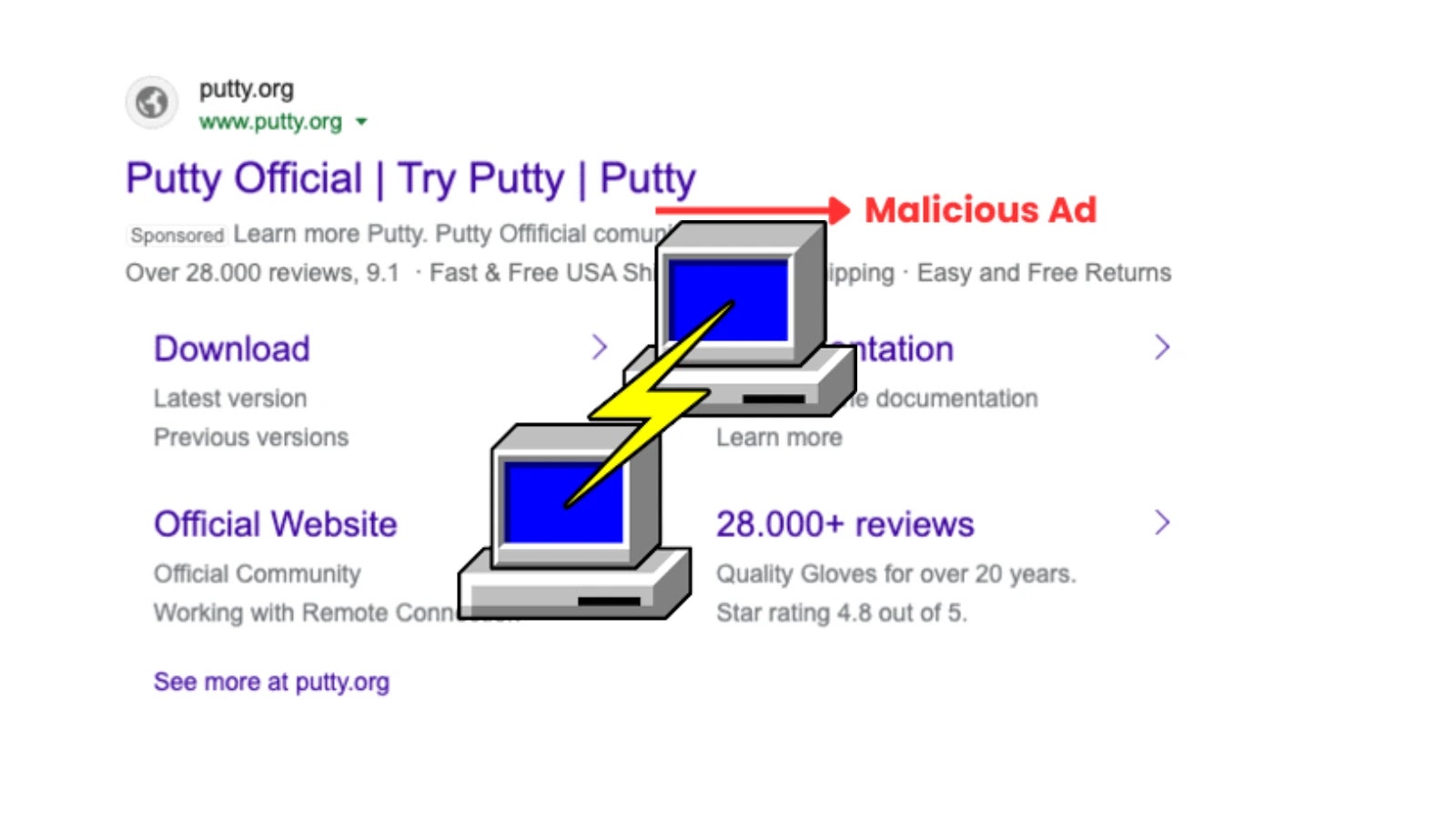
Cyberattacks Exploit Search Results and SEO to Target IT Admins and SMBs
Arctic Wolf researchers have uncovered a sophisticated SEO poisoning campaign targeting IT professionals with fake websites hosting Trojanized versions of PuTTY and WinSCP, leading to backdoor malware infections that can compromise enterprise networks. The campaign exploits search engine results to redirect victims to malicious sites, emphasizing the need for organizations to enforce strict software acquisition policies and deploy network protections to mitigate risks.