"Anatsa Android Malware Spreads to Millions of Samsung Galaxy Users via Google Play"
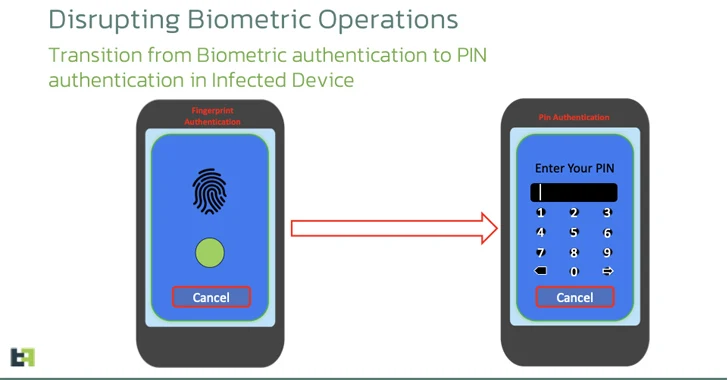
The Anatsa banking trojan has infected at least 150,000 Android devices in Europe through dropper apps hosted on Google Play, targeting specific geographic regions and using tactics to bypass security measures. The malware has evolved to abuse Android’s Accessibility Service and employs a multi-staged infection process. Google has removed most Anatsa dropper apps from the store, but the total number of downloads is expected to increase. Android users are advised to scrutinize app permissions and avoid downloading apps from unfamiliar publishers to protect against potential malware threats.