"Chameleon Android Trojan: Stealing PINs by Bypassing Biometric Authentication"
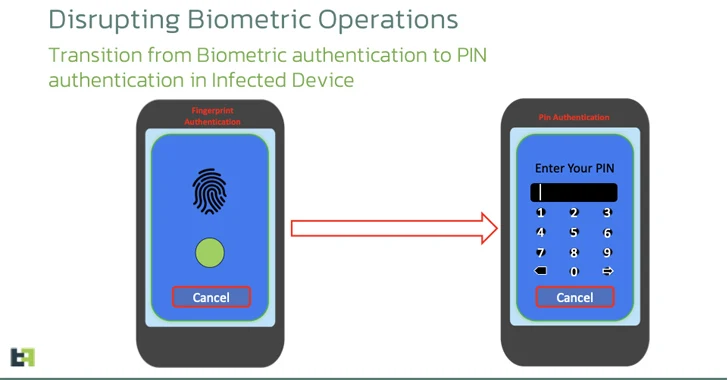
A new variant of the Android banking malware called Chameleon has been discovered, expanding its targeting to users in the U.K. and Italy. This evolved version of Chameleon excels in executing Device Takeover (DTO) using the accessibility service and is now being delivered via Zombinder, a dropper-as-a-service. The malware masquerades as the Google Chrome web browser and tricks users into enabling the accessibility service by checking the Android version on the device. It also disrupts biometric operations by transitioning the lock screen authentication mechanism to a PIN, allowing the malware to unlock the device at will. This development highlights the sophisticated and adaptive nature of the Android threat landscape.
- Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication The Hacker News
- Chameleon Android Trojan Offers Biometric Bypass - Chameleon Android Trojan Offers Biometric Bypass DARKReading
- This nasty Android banking trojan can steal your PIN by disabling fingerprint unlock — how to stay safe Tom's Guide
- Android malware Chameleon disables Fingerprint Unlock to steal PINs BleepingComputer
- A new version of this Android malware can disable fingerprint, face unlock to steal device PIN Times of India
Reading Insights
0
8
3 min
vs 4 min read
83%
656 → 109 words
Want the full story? Read the original article
Read on The Hacker News