Microsoft Fixes Privilege Escalation Flaw in Windows Admin Center (CVE-2026-26119)
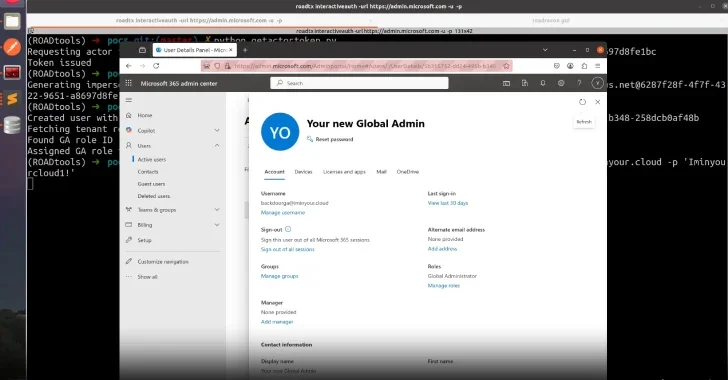
Microsoft patched CVE-2026-26119, a high-severity improper authentication flaw in Windows Admin Center that could allow an authenticated attacker to elevate privileges to the user running the affected app; the fix arrived with Windows Admin Center v2511 (Dec 2025). While there are no confirmed exploits in the wild, Microsoft flags exploitation as more likely and researchers warn it could enable domain compromise under certain conditions.