RisePro Info Stealer Spreading Through GitHub Repositories
TL;DR Summary
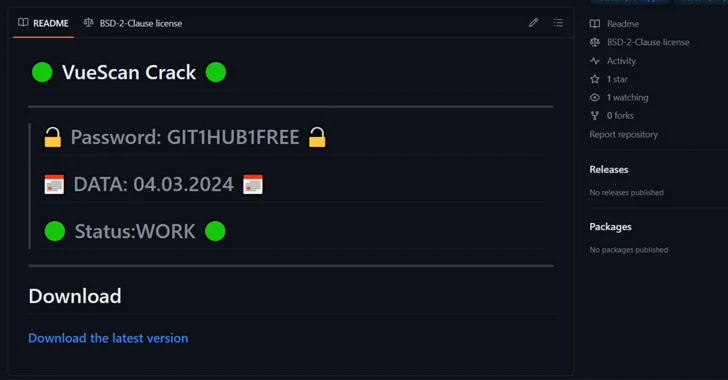
Cybersecurity researchers have discovered GitHub repositories offering cracked software used to distribute the RisePro information stealer. The repositories, which have since been removed, contained RAR archives with an installer file that unpacks the next-stage payload, injecting RisePro into system processes. RisePro is designed to gather sensitive information and exfiltrate it to Telegram channels. This discovery comes amid a rise in popularity of information-stealing malware, which are increasingly used as the primary vector for ransomware and high-impact data breaches.
- Hackers Using Cracked Software on GitHub to Spread RisePro Info Stealer The Hacker News
- Hackers drop RisePro info stealers through GitHub repositories CSO Online
- “gitgub” malware campaign targets Github users with RisePro info-stealer Security Affairs
- Gitgub Campaign Attacking GitHub Users To Steal Login Credentials CybersecurityNews
- RisePro infostealer distributed in GitHub | SC Media SC Media
Reading Insights
Total Reads
0
Unique Readers
1
Time Saved
2 min
vs 3 min read
Condensed
84%
488 → 78 words
Want the full story? Read the original article
Read on The Hacker News