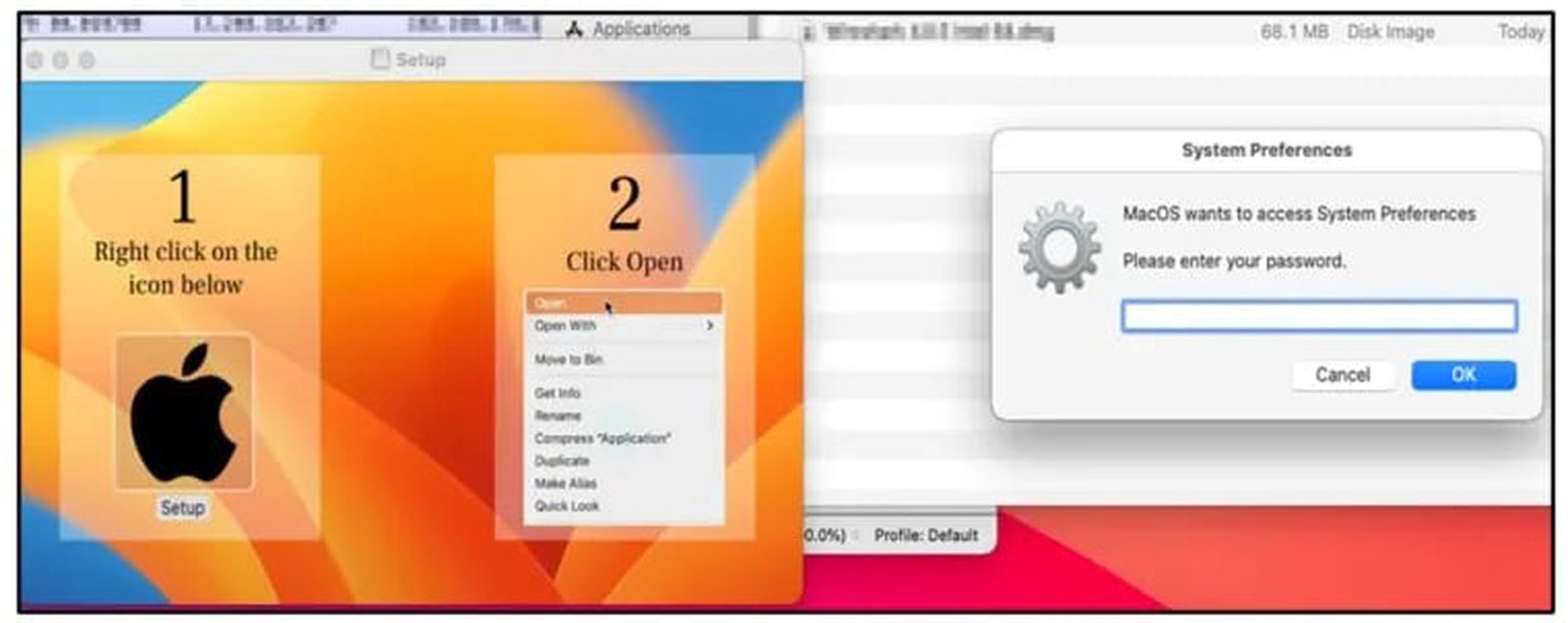
Beware of Atomic macOS Stealer Malware: Your Keychain Passwords and Crypto Wallets at Risk
A new malware called Atomic macOS Stealer (AMOS) is being sold as a service to malicious parties for $1,000/month. If installed, AMOS can compromise a long list of items including iCloud Keychain passwords, the macOS system password, cookies, passwords, and credit card details from various browsers, and crypto wallets. The malware compresses the data into a ZIP file and sends it back to the malicious party through a C&C server URL. It is important to stay diligent and follow best practices such as downloading and installing software only from the official Apple App Store, using strong passwords and multi-factor authentication, and keeping devices and applications updated.