Coordinated DDoS Attacks Knock Arc Raiders and The Finals Offline as Mitigations Roll Out
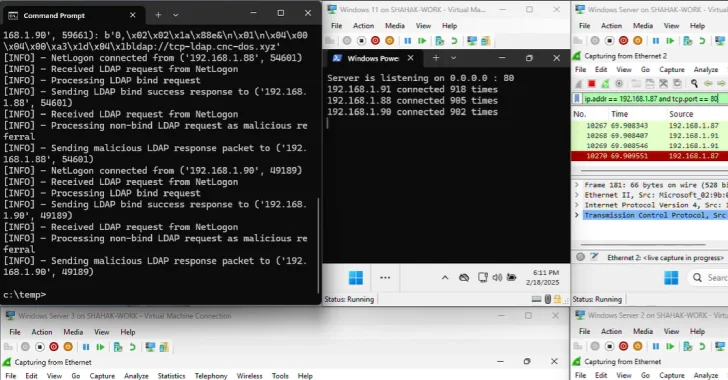
Embark Studios says Arc Raiders and The Finals have been hit by extensive, coordinated DDoS attacks, causing sustained server instability. Mitigations and hotfixes are in progress with some recovery reported, but it’s unclear when full restoration will be complete as players continue to log in.