Microsoft Urges Immediate Updates to Combat New Security Threats
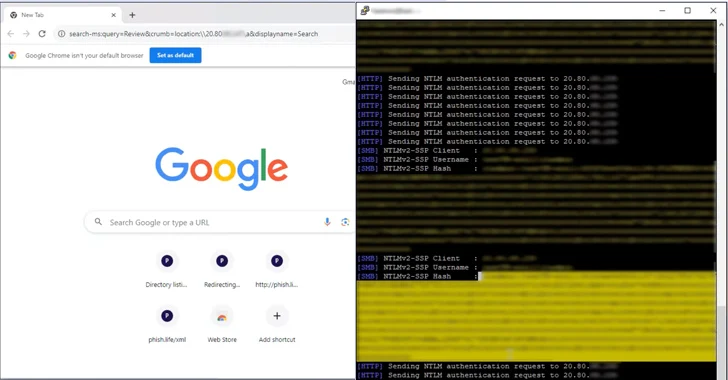
A newly patched NTLM vulnerability, CVE-2024-43451, was exploited by suspected Russian hackers to target Ukraine through phishing emails. The flaw, which allows NTLMv2 hash theft, was used to deliver Spark RAT malware via a compromised Ukrainian government server. The attack involved phishing emails prompting users to download malicious URL files, leading to further payload downloads. CERT-UA linked the activity to Russian threat actor UAC-0194, while also warning of financially motivated attacks using LiteManager software.