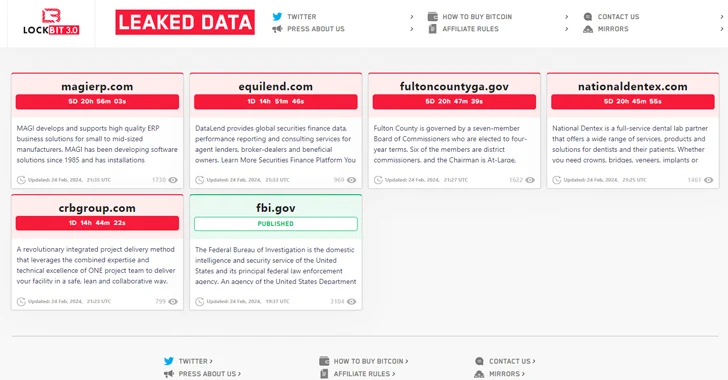
"Ransomware Deadline Passes for Fulton County Amid Trump Document Threat"
Ransomware group LockBit threatened to release stolen data from Fulton County, Ga. unless a ransom was paid, but experts believe the group likely lost the data when its servers were seized by law enforcement. Despite claiming that the county had paid, officials stated they did not make any payments. The FBI and U.K.’s National Crime Agency took over LockBit’s infrastructure, and the group reemerged with new deadlines for data release. However, experts believe LockBit's recent activities are attempts to save face, and it's likely the end of the LockBit brand.