The Evolution of Rhadamanthys Stealer: A Powerful Swiss Army Knife of Malware
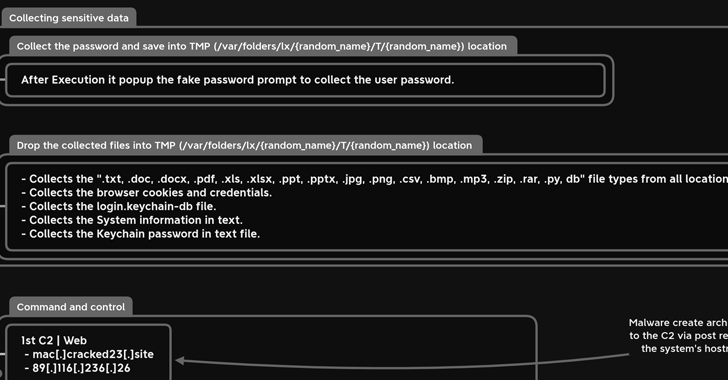
The developers of the Rhadamanthys information-stealing malware have released two major versions, introducing new stealing capabilities and enhanced evasion techniques. The malware, sold via a subscription model, targets email, FTP, and online banking service account credentials. The latest versions feature a new plugin system for customization, improved stub construction, and client execution process, as well as fixes for targeting cryptocurrency wallets. Rhadamanthys also includes passive and active stealers for data exfiltration, with the ability to evade Windows Defender. The rapid development of Rhadamanthys makes it an increasingly attractive tool for cybercriminals.