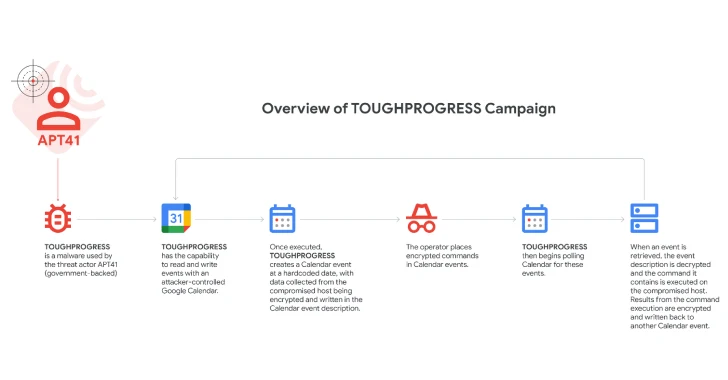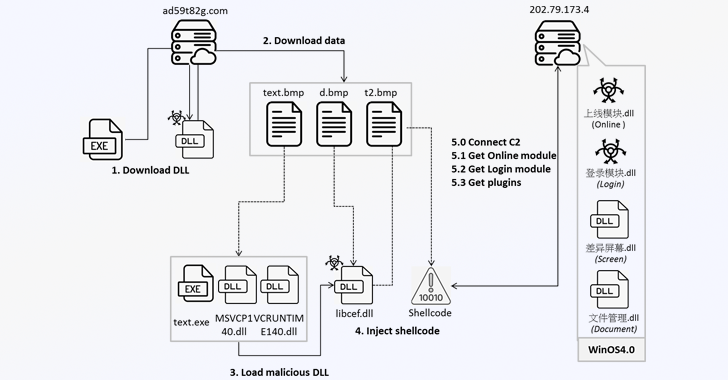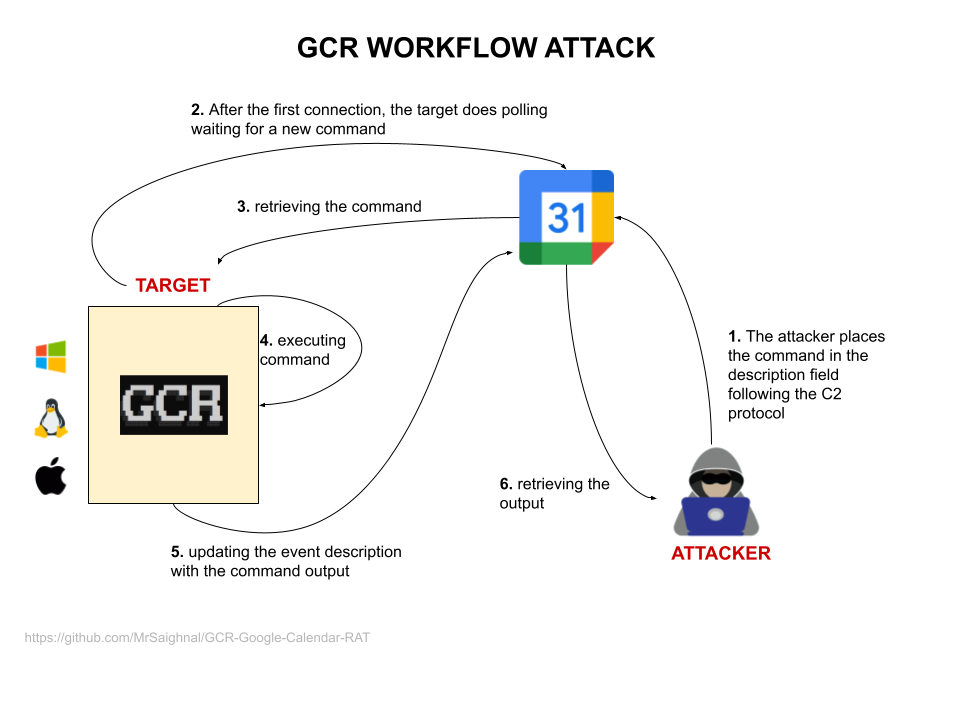
AI Assistants Turned Stealthy Malware Relays for C2 Traffic
Researchers show that AI assistants like Grok and Microsoft Copilot can be abused as covert command-and-control relays for malware, directing the AI to fetch attacker-controlled URLs and relay results back via WebView2, potentially bypassing safeguards; Microsoft acknowledges the risk and recommends defense-in-depth to block infections and limit post-compromise activity.