Google Calendar Exploited by Hackers as Covert C2 Channel
TL;DR Summary
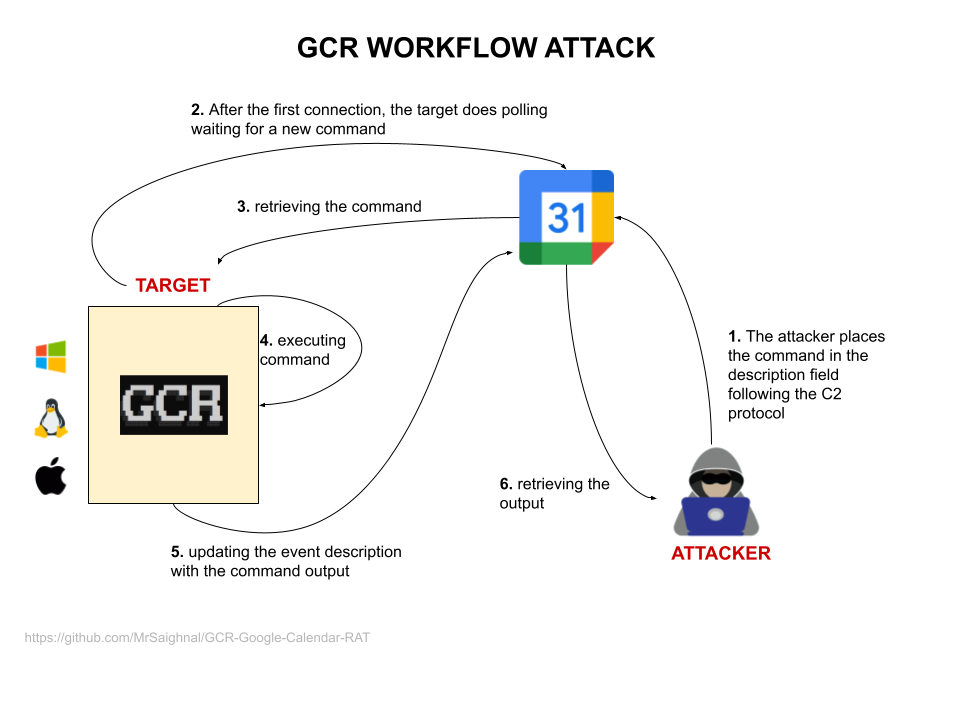
Google warns of threat actors using a public proof-of-concept exploit called Google Calendar RAT, which utilizes the Calendar service as a command-and-control (C2) infrastructure. The exploit creates a covert channel by exploiting event descriptions in Google Calendar, making it difficult for defenders to detect malicious activity. While Google has not observed the use of Google Calendar RAT in the wild, Mandiant has seen multiple actors sharing the exploit on underground forums. This follows previous instances of threat actors abusing Google services for their operations.
- Attackers use Google Calendar RAT to abuse Calendar service as C2 infrastructure Security Affairs
- Even Google Calendar isn't safe from hackers any more TechRadar
- Google Calendar Is a Potential Tool for Hackers to Control Malware PCMag
- Novel Google Cloud RAT Uses Calendar Events for C2 DARKReading
- Google Warns How Hackers Could Abuse Calendar Service as a Covert C2 Channel The Hacker News
- View Full Coverage on Google News
Reading Insights
Total Reads
0
Unique Readers
1
Time Saved
1 min
vs 2 min read
Condensed
77%
359 → 84 words
Want the full story? Read the original article
Read on Security Affairs