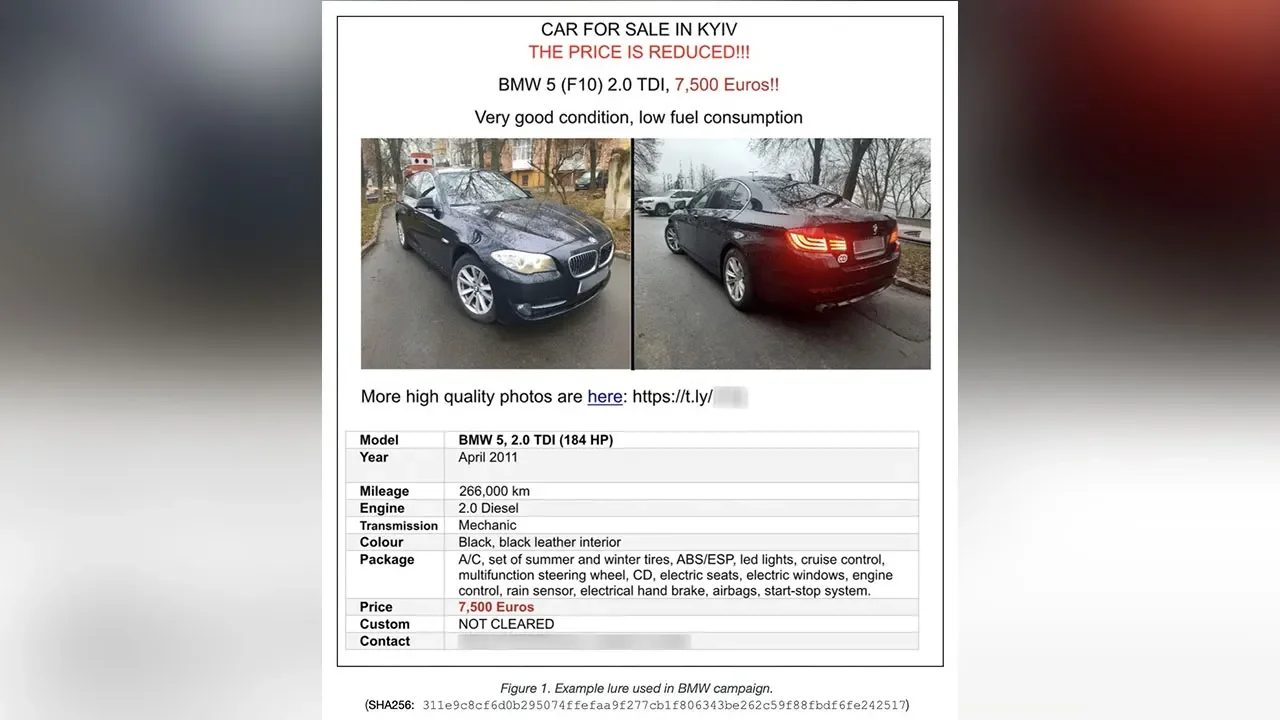
"Five Eyes Allies Warn of Russian Hackers' Shifting Tactics to Target Cloud Environments"
The Five Eyes intelligence alliance has issued a warning that APT29 Russian hackers, also known as Cozy Bear, have shifted their focus to targeting victims' cloud services, using various tactics such as exploiting compromised credentials, dormant accounts, and stolen access tokens. The alliance advises network defenders to implement multi-factor authentication, strong passwords, least privilege access, and other security measures to mitigate the threat of APT29's cloud attacks.