Russian Hackers Exploit Fresh Office Flaw Hours After Patch
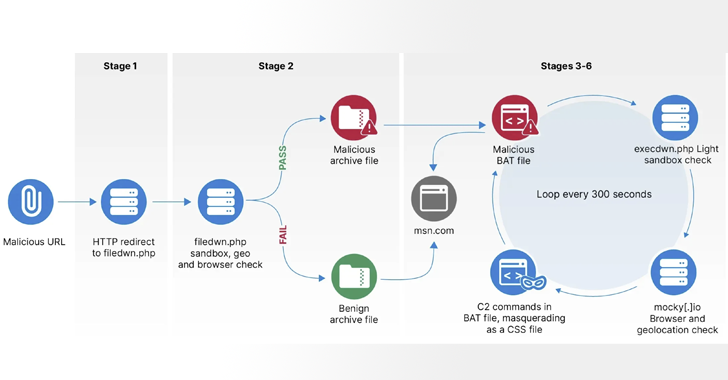
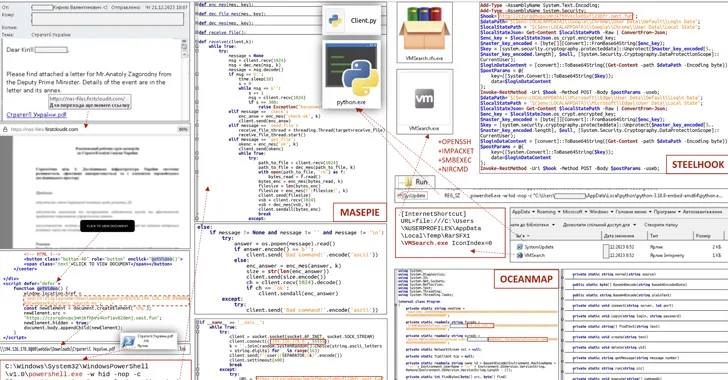
Within 48 hours of Microsoft issuing an urgent Office patch for CVE-2026-21509, the Russian-state group APT28 launched a fast, in-memory, fileless campaign that installed new backdoors (BeardShell and NotDoor) via staged spear-phishing across nine countries, targeting defense ministries, transportation operators, and diplomatic entities, with command-and-control hosted on legitimate cloud services to evade detection.