Russian Hackers Disrupted After Targeting Europe and Ukraine with Malware and Phishing
TL;DR Summary
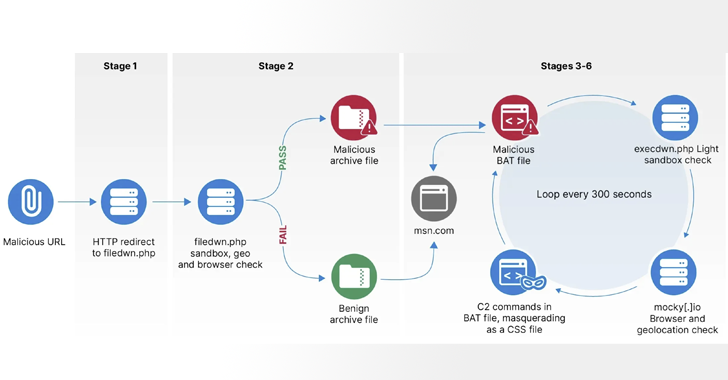
The Russian GRU-backed APT28 group, also known as BlueDelta, has been targeting European networks, particularly in Ukraine, with the HeadLace malware and credential-harvesting web pages. The campaigns, running from April to December 2023, utilized spear-phishing emails and sophisticated multi-stage infection sequences. BlueDelta's operations aimed to gather intelligence on military-related entities, employing various techniques including geofencing, legitimate internet services, and compromised Ubiquiti routers. The group's activities reflect a broader strategy to influence military tactics and regional policies amidst ongoing aggression against Ukraine.
Topics:world#apt28#credential-harvesting#cyber-attack-credential-harvesting#europe#headlace#russian-hackers
- Russian Hackers Target Europe with HeadLace Malware and Credential Harvesting The Hacker News
- GRU's BlueDelta Targets Key Networks in Europe with Multi-Phase Espionage Camp Recorded Future
- FlyingYeti phishing crew grounded after abominable Ukraine attacks The Register
- Russia-linked hackers' phishing campaign against Ukraine is disrupted NPR
- FlyingYeti APT Serves Up Cookbox Malware Using WinRAR Dark Reading
Reading Insights
Total Reads
0
Unique Readers
8
Time Saved
2 min
vs 3 min read
Condensed
85%
530 → 81 words
Want the full story? Read the original article
Read on The Hacker News