"Chinese Hackers Infiltrate US Infrastructure, FBI Chief Warns of Potential Devastating Cyberattack"
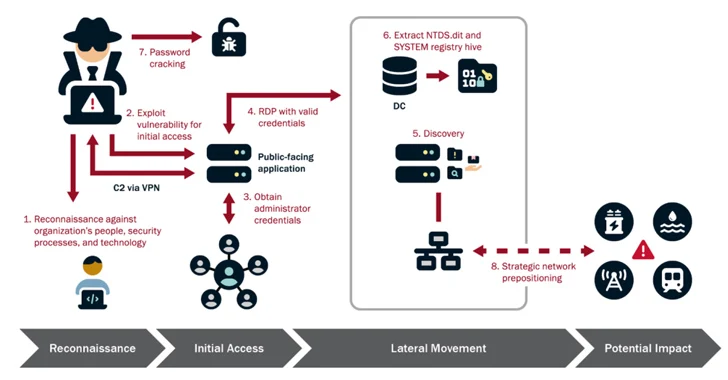
FBI director Christopher Wray warned that Chinese hackers have infiltrated US critical infrastructure, targeting companies in telecommunications, energy, water, and 23 pipeline operators, with the intent to potentially cause devastating damage. China's broader intent is seen as a means to deter the US from defending Taiwan, although China denies government involvement and claims the hacking is unrelated to them. The hackers operate botnets to conceal their activities, and private sector companies have attributed the attacks to China.