Identity as the Perimeter: The Hidden Gate in Cyber Breaches
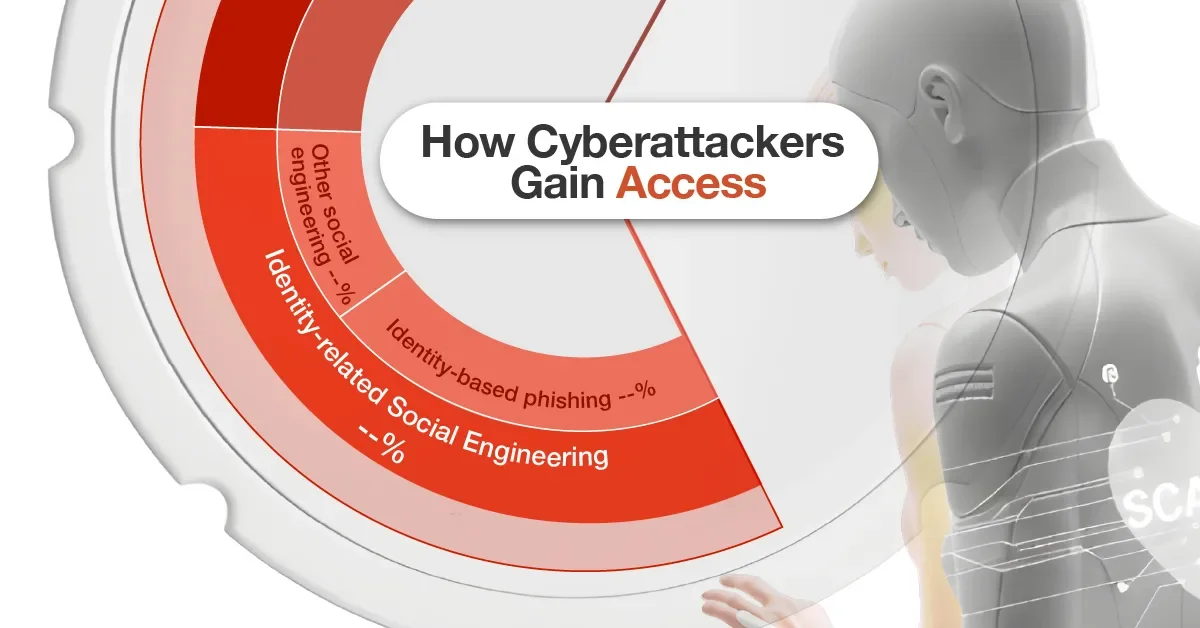
A sponsored Visual Capitalist infographic (in partnership with Unit 42 by Palo Alto Networks) outlines how cyberattackers breach systems by exploiting identity. Identity-based techniques drive about 65% of initial access, with social engineering and credential misuse leading the way, and 90% of recent investigations showing identity weaknesses as material. Once inside, over-privileged identities and token abuse enable rapid lateral movement, making identity the practical perimeter. Defenses recommended include phishing-resistant MFA (passkeys/FIDO2), rotating machine credentials, shorter sessions, just-in-time elevation for admins, and cross-cloud identity telemetry to detect unusual access chains.














