Santander Data Breach: Hackers Selling 30M Customer Records
Hackers are offering to sell stolen customer and staff details from Santander, raising significant cybersecurity concerns for the bank and its clients.
All articles tagged with #customer information
Hackers are offering to sell stolen customer and staff details from Santander, raising significant cybersecurity concerns for the bank and its clients.

AT&T confirms a data breach affecting over 7.6 million current and 65 million former customers, leading to the reset of security passcodes for active customers. The leaked information may include personal details such as names, email addresses, social security numbers, and more. The company is notifying affected customers and offering free fraud alerts from credit bureaus. AT&T is working with cybersecurity experts to analyze the situation and has found no evidence of authorized access to its systems.

LoanDepot disclosed that 16.6 million customers had their "sensitive personal" information stolen in a ransomware attack, with the company working to notify affected customers and restore normal business operations. The specific types of customer data taken have not been disclosed, and many online services remain inaccessible. The company has not yet determined the potential financial impact of the cybersecurity incident.

Framework Computer, a laptop manufacturer, disclosed a data breach affecting an undisclosed number of customers after its accounting service provider, Keating Consulting Group, fell victim to a phishing attack. An attacker impersonating Framework's CEO tricked a Keating Consulting accountant into sharing a spreadsheet containing customers' personally identifiable information. The company has notified affected individuals and is warning them of potential phishing risks. Additionally, all employees with access to customer information will undergo mandatory phishing and social engineering attack training, and the company is auditing the procedures of other consultants who had access to customer information.

U.S. mortgage lender loanDepot has been hit by a cyberattack, causing IT systems to go offline and impacting the payment portal, with customers experiencing difficulties making payments and contacting the company. While the nature of the attack is not confirmed, it is suspected to be a ransomware attack, potentially exposing sensitive customer data. This incident follows a data breach in May, and customers are advised to remain vigilant for potential phishing attacks and identity theft.

Comcast and Xfinity customers in Michigan are advised to check their information following a national data breach. Hackers gained access to usernames, passwords, contact information, social security numbers, and birthdates of over 35 million Xfinity customers. The attorney general's office recommends changing passwords, watching out for phishing emails, using multifactor authentication, and reviewing credit reports regularly. Customers with questions can contact Xfinity, and complaints can be filed with the attorney general's office.

Hackers exploited a vulnerability in a third-party vendor, Citrix, that serviced Xfinity, potentially compromising the personal information of approximately 36 million customers. Xfinity initially patched the system, but unauthorized access to internal systems occurred between October 16 and October 19, 2023, resulting in the likely acquisition of customer data. Stolen information includes usernames, passwords, names, contact information, last four digits of social security numbers, dates of birth, and secret questions. Xfinity advises customers to reset their passwords and emphasizes its commitment to protecting customer information. Comcast, Xfinity's parent company, has not commented on the incident, and Citrix has yet to respond to requests for comment.

Hackers exploited a critical security vulnerability known as "CitrixBleed" to gain access to the sensitive information of nearly 36 million Xfinity customers. The vulnerability, found in Citrix networking devices, has been under mass-exploitation since August. Xfinity confirmed that hackers had access to its internal systems between October 16 and 19, but the malicious activity was not detected until October 25. Customer data, including usernames, hashed passwords, names, contact information, dates of birth, and partial Social Security numbers, may have been accessed. Comcast has not disclosed the exact number of affected customers but confirmed that almost 35.8 million customers are impacted. The company is requiring customers to reset their passwords and recommends the use of two-factor authentication.

Xfinity, the cable communications company, has disclosed a data breach after attackers breached one of its Citrix servers in October. The breach, which exploited a vulnerability known as Citrix Bleed, resulted in the theft of customer-sensitive information, including usernames, hashed passwords, and potentially other personal details such as names, contact information, and social security numbers. Xfinity has asked affected users to reset their passwords, although some customers reported receiving password reset requests without explanation. This incident follows a previous credential stuffing attack on Xfinity accounts a year ago. The company claims that its operations were not impacted, and it has not received any ransom demands.

Xfinity has disclosed a data breach that occurred from October 16th to October 19th, 2023, resulting in the theft of customer information, including usernames, passwords, contact information, and more. The breach was traced back to a security vulnerability disclosed by Citrix. While the number of affected users is still unknown, Xfinity has notified federal law enforcement and is urging customers to change their passwords and enable two-factor authentication. The company claims that no customer data has been leaked or attacked, and their cybersecurity team is actively monitoring the situation.

Mortgage and loan giant Mr. Cooper experienced a cyberattack at the end of October, potentially impacting over 14 million customers. The breach involved unauthorized access to sensitive personal information, including names, addresses, phone numbers, Social Security numbers, and bank account numbers. The company shut down its systems to contain the incident and is actively investigating the breach. Mr. Cooper is monitoring the dark web for any further misuse of the data and is updating its systems to prevent future breaches. The company's CEO expressed apologies and reassured customers of their commitment to resolving the issue.

Okta has revealed that the October 2023 breach of its support case management system had a broader impact than initially reported. The threat actor downloaded the names and email addresses of all Okta customer support system users, affecting all Okta Workforce Identity Cloud (WIC) and Customer Identity Solution (CIS) customers except those in separate support systems. Additionally, reports containing contact information of Okta certified users, some CIC customers, and unspecified employee information were accessed. However, no user credentials or sensitive personal data were compromised. Okta has notified customers of potential phishing risks and implemented new security features. The identity of the threat actors is unknown, but a cybercrime group called Scattered Spider has targeted Okta in the past.
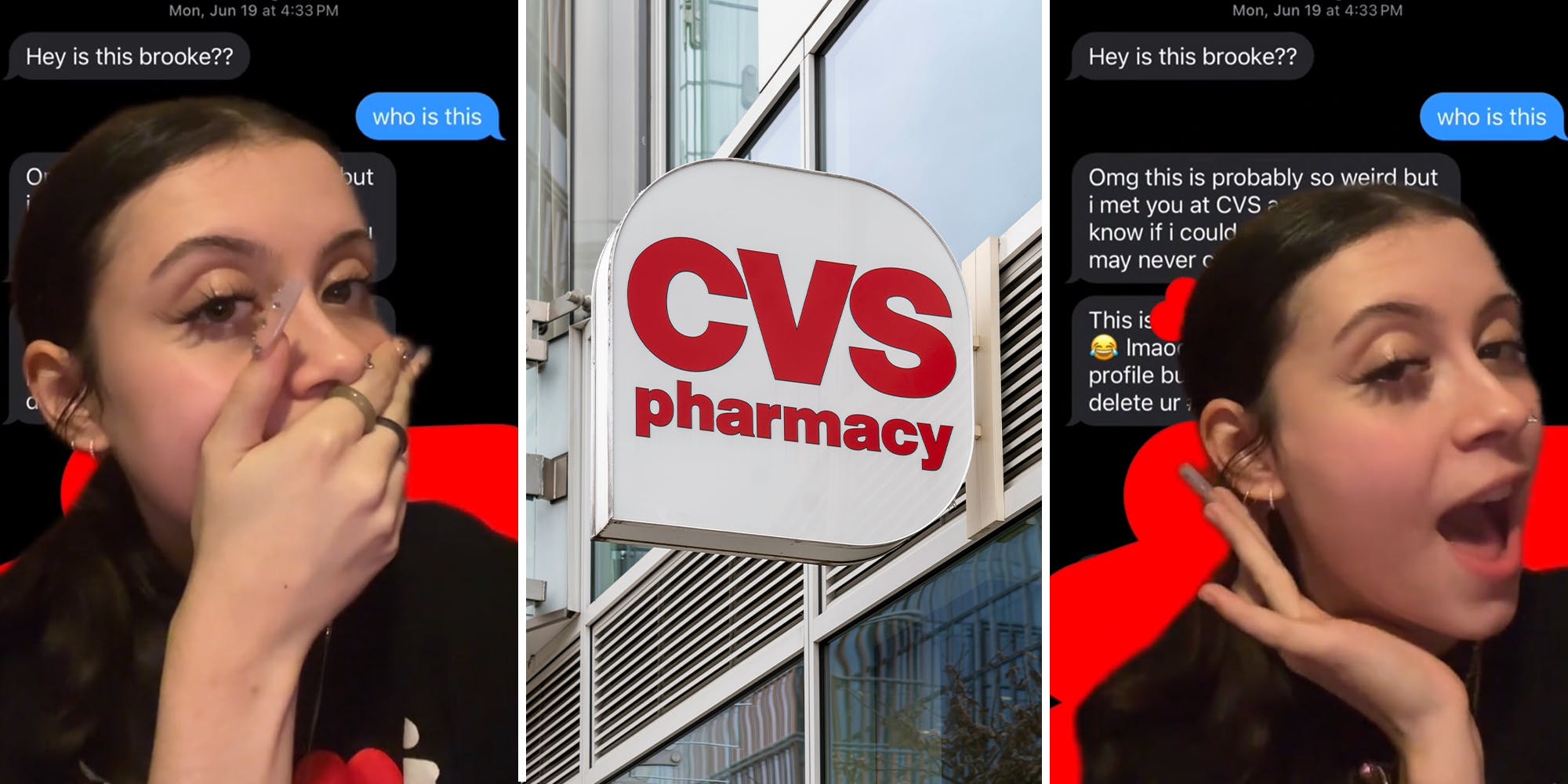
A TikTok user claims that a CVS pharmacist obtained her phone number from the store's system after she refused to give it to him. The user shared a text message exchange where the pharmacist mentioned meeting her at CVS. Other commenters on TikTok shared similar experiences of individuals using customer information to contact them. Some suggested reporting the incident to CVS and getting the pharmacist fired.

Walmart customers in Central New York are concerned about their credit card information being stolen after card skimming devices were found at five Walmart stores. Despite requests for information, Walmart has refused to answer questions about the incident, leaving customers uncertain about the extent of the breach and what actions they should take. Police are seeking the public's help in identifying the suspects responsible for installing the skimmers. Skimming devices capture card data and can be used to create fake cards, resulting in financial losses for victims.

Toyota disclosed a data breach that exposed the car-location information of 2.15 million customers for ten years due to a database misconfiguration that allowed anyone to access its contents without a password. The exposed information includes the in-vehicle GPS navigation terminal ID number, the chassis number, and vehicle location information with time data. While there is no evidence that the data was misused, unauthorized users could have accessed the historical data and possibly the real-time location of Toyota cars. Toyota has promised to send individual apology notices to impacted customers and set up a dedicated call center to handle their queries and requests.