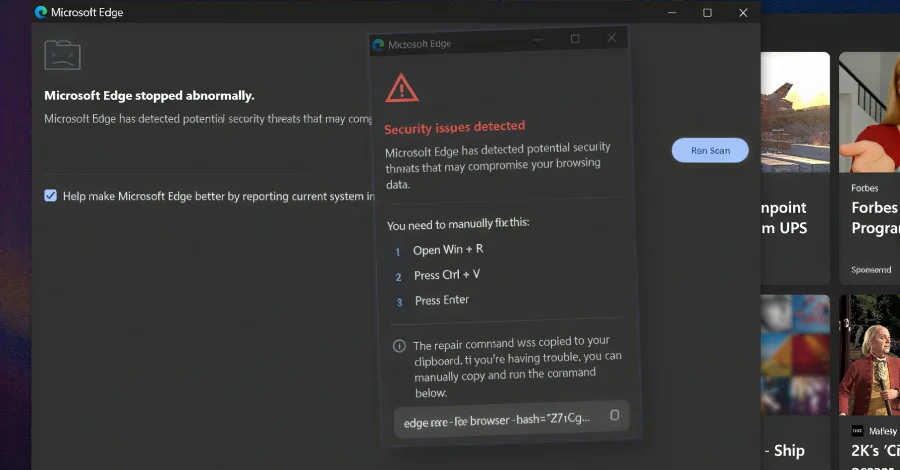
CrashFix Chrome Campaign Traps Users With DoS Crash to Deliver ModeloRAT
Security researchers detail KongTuke's CrashFix campaign, where a counterfeit Chrome extension named NexShield clones uBlock Origin Lite, issues a fake security warning, and triggers a DoS-style crash to coerce users into running a command. The attack uses a 60-minute delayed, multi-stage payload that reports a unique ID to nexsnield[.]com, fetches subsequent stages via PowerShell, and loads the ModeloRAT payload on domain-joined machines via RC4-encrypted C2 and Registry persistence; standalone hosts see a testing payload first. The operation leverages a traffic distribution system and underscores evolving social engineering and self-sustaining infection loops.
