Android Malware Apps Evade Detection with Stealthy APK Compression
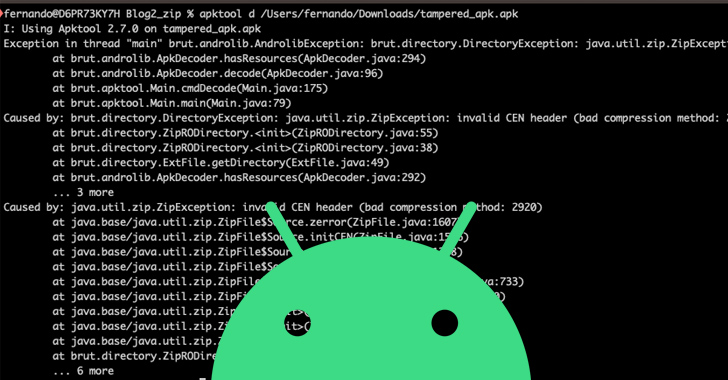
Threat actors are using Android Package (APK) files with unsupported compression methods to evade malware analysis. Over 3,300 artifacts have been found using this technique, with 71 samples able to be loaded onto the operating system without issues. These apps were likely distributed through untrusted app stores or social engineering tactics. The use of unsupported compression methods limits decompilation and analysis, making it difficult to detect and analyze the malware. Additionally, malware authors are deliberately corrupting APK files to trigger crashes on analysis tools. This discovery follows Google's recent revelation about threat actors using versioning to bypass malware detection on the Play Store.
- Thousands of Android Malware Apps Using Stealthy APK Compression to Evade Detection The Hacker News
- Thousands of Android malware apps use stealthy APKs to bypass security, study finds Tom's Guide
- Be careful what you download, there is a new Android malware on the loose! PhoneArena
- Thousands of Android APKs Use Compression Methods to Evade Malware Analysis PhoneWorld Magazine
- Thousands of Android APKs use compression trick to thwart analysis BleepingComputer
Reading Insights
0
9
1 min
vs 2 min read
69%
335 → 103 words
Want the full story? Read the original article
Read on The Hacker News