"New Malware Bypasses Password Changes by Exploiting Google OAuth to Hijack Accounts"
TL;DR Summary
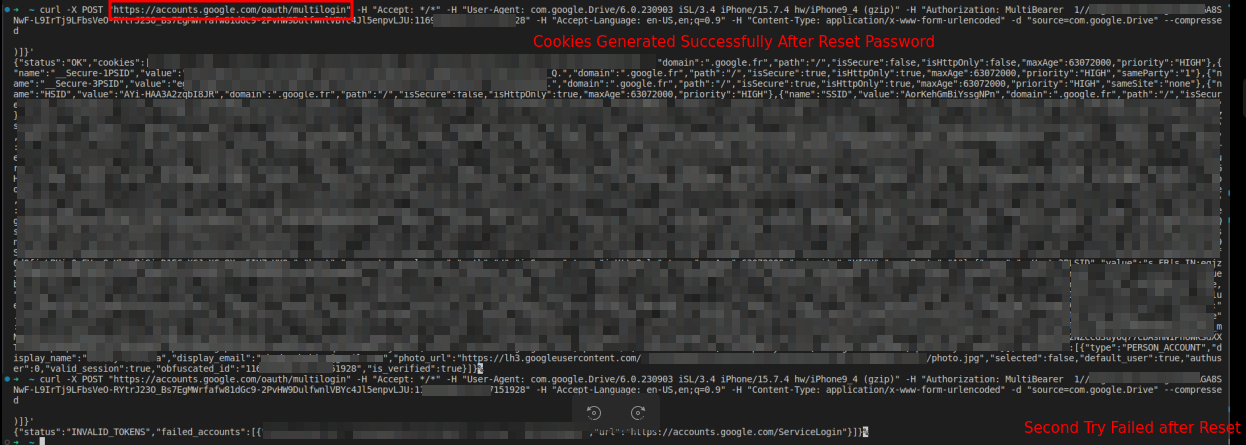
CloudSEK researchers have reverse-engineered a zero-day exploit that leverages an undocumented Google OAuth endpoint, 'MultiLogin,' to regenerate persistent Google cookies even after password resets. Initially discovered by a developer named PRISMA, the exploit has been used by various malware, including Lumma Infostealer and White Snake, to maintain access to Google services. The exploit manipulates token:GAIA ID pairs extracted from Chrome's token_service table, allowing attackers to persistently exploit user accounts. Google has not yet confirmed the exploitation of this vulnerability.
- Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies Security Affairs
- Google accounts may be vulnerable to new hack, changing password won’t help CyberNews.com
- Malware abuses Google OAuth endpoint to ‘revive’ cookies, hijack accounts BleepingComputer
- A new malware is affecting Google Chrome, enabling access to login tokens and accounts Times of India
- New malware restores cookies to break into your Google Account 9to5Google
Reading Insights
Total Reads
0
Unique Readers
6
Time Saved
1 min
vs 2 min read
Condensed
79%
375 → 79 words
Want the full story? Read the original article
Read on Security Affairs