"Security Risks in ChatGPT Plugins Expose Data and Accounts"
TL;DR Summary
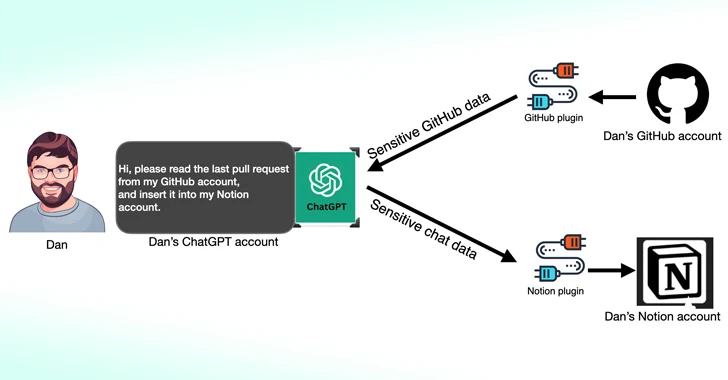
Third-party plugins for OpenAI ChatGPT could be exploited by threat actors to hijack accounts on third-party websites, such as GitHub, and access sensitive data. Security flaws in ChatGPT and its ecosystem, including OAuth manipulation and zero-click account takeover vulnerabilities, have been uncovered by Salt Labs. Additionally, a new side-channel attack has been identified, allowing attackers to extract encrypted responses from AI assistants by inferring token lengths in network traffic. Countermeasures such as random padding and transmitting tokens in larger groups are recommended to mitigate the effectiveness of the side-channel attack.
- Third-Party ChatGPT Plugins Could Lead to Account Takeovers The Hacker News
- Critical ChatGPT Plug-in Vulnerabilities Expose Sensitive Data Dark Reading
- ChatGPT 0-click plugin exploit risked leak of private GitHub repos SC Media
- Salt Security Uncovers Security Flaws within ChatGPT Extensions that Allowed Access to Third-Party Websites and Sensitive Data - Issues have been Remediated Yahoo Finance
- ChatGPT Plugin Vulnerabilities Exposed Data, Accounts SecurityWeek
Reading Insights
Total Reads
0
Unique Readers
6
Time Saved
3 min
vs 4 min read
Condensed
88%
729 → 90 words
Want the full story? Read the original article
Read on The Hacker News