"China-linked Hackers Target Guyana Government with DinodasRAT in Operation Jacana"
TL;DR Summary
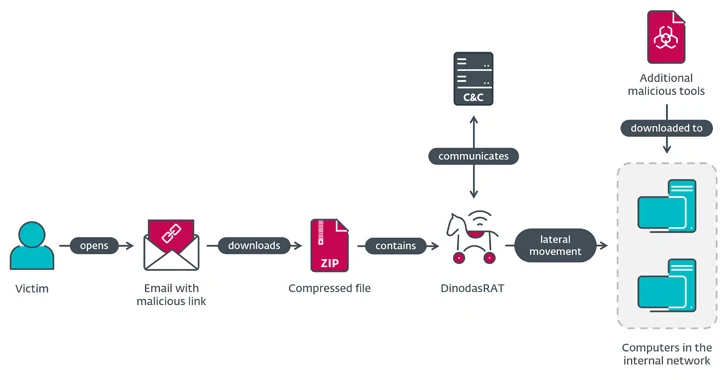
A governmental entity in Guyana has been targeted in a cyber espionage campaign called Operation Jacana. The attack involved a spear-phishing email that led to the deployment of a previously undocumented implant called DinodasRAT. The campaign is attributed with medium confidence to a China-nexus adversary due to the use of the remote access trojan PlugX. The attackers used a combination of DinodasRAT and traditional backdoors like Korplug, and they tailored their emails to entice their chosen victim organization. The attackers are monitoring the geopolitical activities of their victims to increase the success of their operation.
Topics:technology#china-nexus-adversary#cyber-espionage#cyber-threat#dinodasrat#guyana#spear-phishing
- Guyana Governmental Entity Hit by DinodasRAT in Cyber Espionage Attack The Hacker News
- DinodasRAT used against governmental entity in Guayana – Week in security with Tony Anscombe We Live Security
- 'Operation Jacana' Reveals DinodasRAT Custom Backdoor DARKReading
- Suspected China-linked hackers target Guyana government with new backdoor The Record from Recorded Future News
- Operation Jacana: Foundling hobbits in Guyana We Live Security
- View Full Coverage on Google News
Reading Insights
Total Reads
0
Unique Readers
8
Time Saved
1 min
vs 2 min read
Condensed
74%
370 → 95 words
Want the full story? Read the original article
Read on The Hacker News