Iranian Hackers Target Israel with Sophisticated Techniques and Backdoors.
TL;DR Summary
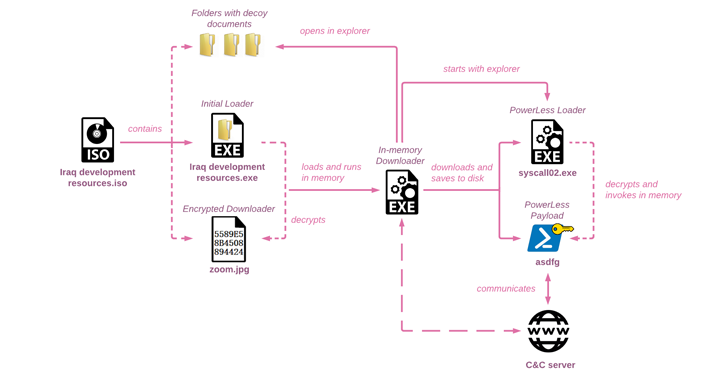
Iranian hackers, believed to be linked to APT35, have launched a new wave of phishing attacks targeting Israel using an updated version of the PowerLess backdoor. The attacks use ISO images and other archive files to initiate infection chains, with the PowerLess implant being launched via a custom in-memory downloader. The malware is capable of stealing data from web browsers and apps, taking screenshots, recording audio, and logging keystrokes. The attackers are continuously refining their malware arsenal to expand their functionality and resist analysis efforts, while also adopting enhanced methods to evade detection.
- Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor The Hacker News
- US military kicked Iranian hackers off municipal website reporting unofficial election results in 2020 CNN
- Iranians hacked election results computer in 2020, but were blocked The Washington Post
- Iranian Hackers "Educated Manticore" Target Israel With New Tools Infosecurity Magazine
- Check Point Research uncovers rare techniques used by Iranian-affiliated threat actor, targeting Israeli entities Check Point Blog
Reading Insights
Total Reads
0
Unique Readers
0
Time Saved
2 min
vs 3 min read
Condensed
83%
553 → 93 words
Want the full story? Read the original article
Read on The Hacker News