TP-Link Routers Targeted by Persistent Attacks from Camaro Dragon and Mustang Panda Hackers.
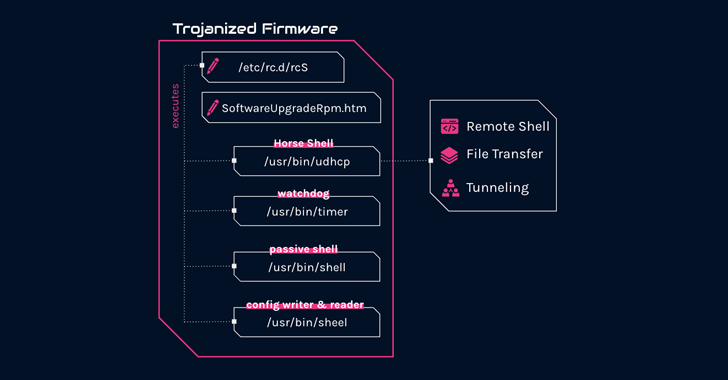
Chinese state-sponsored hacking group Mustang Panda, also known as Camaro Dragon, has been linked to a new set of targeted attacks on European foreign affairs entities using a custom firmware implant designed for TP-Link routers. The implant features a backdoor named 'Horse Shell' that enables the attackers to maintain persistent access, build anonymous infrastructure, and enable lateral movement into compromised networks. The router backdoor is believed to target arbitrary devices on residential and home networks, suggesting that the compromised routers are being co-opted into a mesh network with the goal of creating a "chain of nodes between main infections and real command-and-control."
- China's Mustang Panda Hackers Exploit TP-Link Routers for Persistent Attacks The Hacker News
- The Dragon Who Sold His Camaro: Analyzing Custom Router Implant Check Point Research
- Hackers infect TP-Link router firmware to attack EU entities BleepingComputer
- Camaro Dragon APT Group Exploits TP-Link Routers With Custom Implant Infosecurity Magazine
- View Full Coverage on Google News
Reading Insights
0
1
2 min
vs 3 min read
80%
522 → 102 words
Want the full story? Read the original article
Read on The Hacker News