QBot Trojan Spreading Through Business Emails with New Tactics
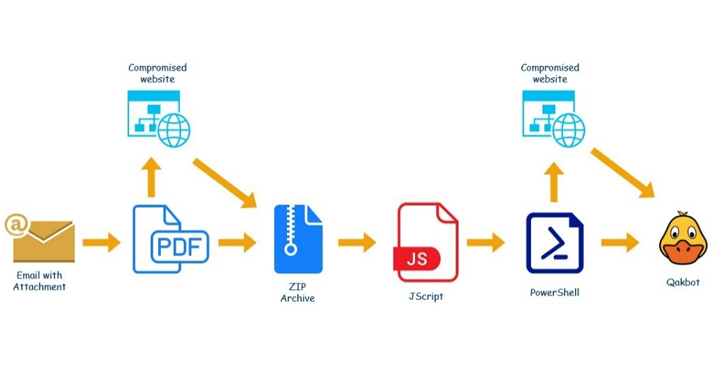
A new QBot malware campaign is using hijacked business emails to spread malware, primarily targeting users in Germany, Argentina, Italy, Algeria, Spain, the U.S., Russia, France, the U.K., and Morocco. QBot is a banking trojan that steals passwords and cookies from web browsers and doubles up as a backdoor to inject next-stage payloads such as Cobalt Strike or ransomware. The malware is distributed via phishing campaigns and has seen constant updates during its lifetime to evade detection. The latest campaign uses email thread hijacking attacks to trick victims into opening a malicious PDF file that leads to the retrieval of an archive file containing an obfuscated Windows Script File that downloads the QBot malware.
- New QBot Banking Trojan Campaign Hijacks Business Emails to Spread Malware The Hacker News
- New QBot email attacks use PDF and WSF combo to install malware BleepingComputer
- Qbot Banking Trojan Increasingly Delivered Via Business Emails Infosecurity Magazine
Reading Insights
0
0
1 min
vs 2 min read
69%
362 → 114 words
Want the full story? Read the original article
Read on The Hacker News